
Any device or software application that detects and monitors policy violations or any malicious activities is called an intrusion detection system. Typically, any violation or malicious activities are collected or reported centrally using a security and event management system.
Moreover, some intrusion detection systems can detect as well as respond to intrusions when they are discovered. There are different classifications of intrusion detection systems and let’s find out what they are.
Basically, there are various Intrusion Detection Systems, ranging from tiered monitoring systems that monitor the entire network traffic to antivirus software. However, the most common classifications are:
Furthermore, there are also variants or subsets of Intrusion Detection Systems. The most common ones are:
The term ‘signature’ originates from detected patterns in antivirus software known as signatures. In spite of the fact that signature-based IDS can detect known attacks, it is nearly impossible to detect new attacks whose patterns are currently unknown.
However, there is a chance of getting false positive as legitimate activities that were previously unknown can be accidentally classified as malicious.
Cybercriminals trying to breach your secure network can use various evasion techniques. Being aware of these techniques can help your IT department to understand how the IDS systems can be deceived into passing on some actionable threats.
So, here are some such techniques that cyber criminals can use.
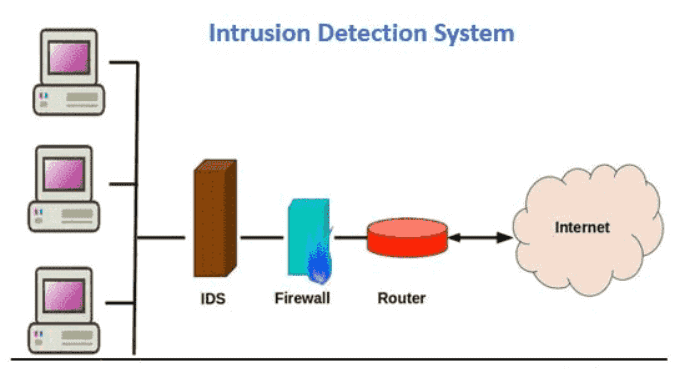
An IDS will perform an analysis of passing traffic and match the traffic that is passed on the subnets to the library of known attacks, when placed at strategic points within a network to monitor traffic from all devices on the network.
Once an abnormal behavior is sensed or an attack is identified, an alert is sent to the administrator.
High level security is a must have for any modern networked business environment. It ensures trusted and safe communication within as well as between the organizations.
If in any case, traditional technologies fail, an intrusion detection systems can act as an adaptable safeguard technology. It is for sure that cyber attacks will become more sophisticated, therefore, it is also important that the protection technologies evolve along the way to adapt to these newer threats.
Sign up to stay updated with the latest insights, news, and more.